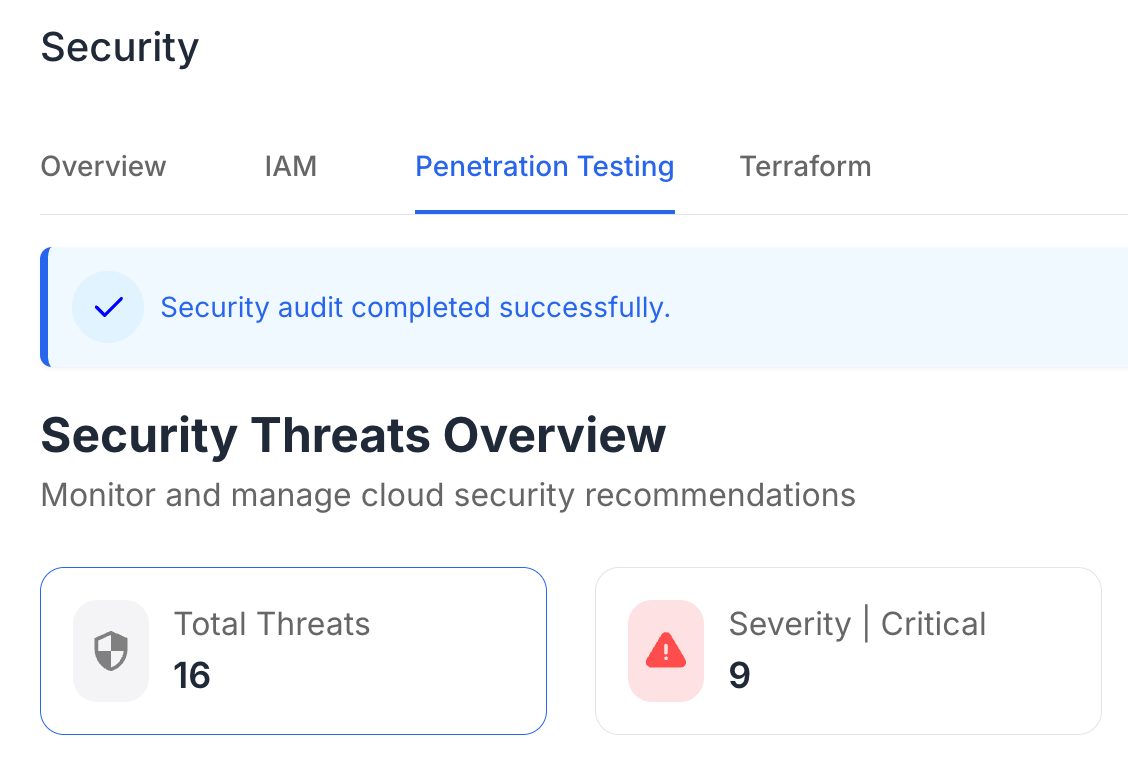
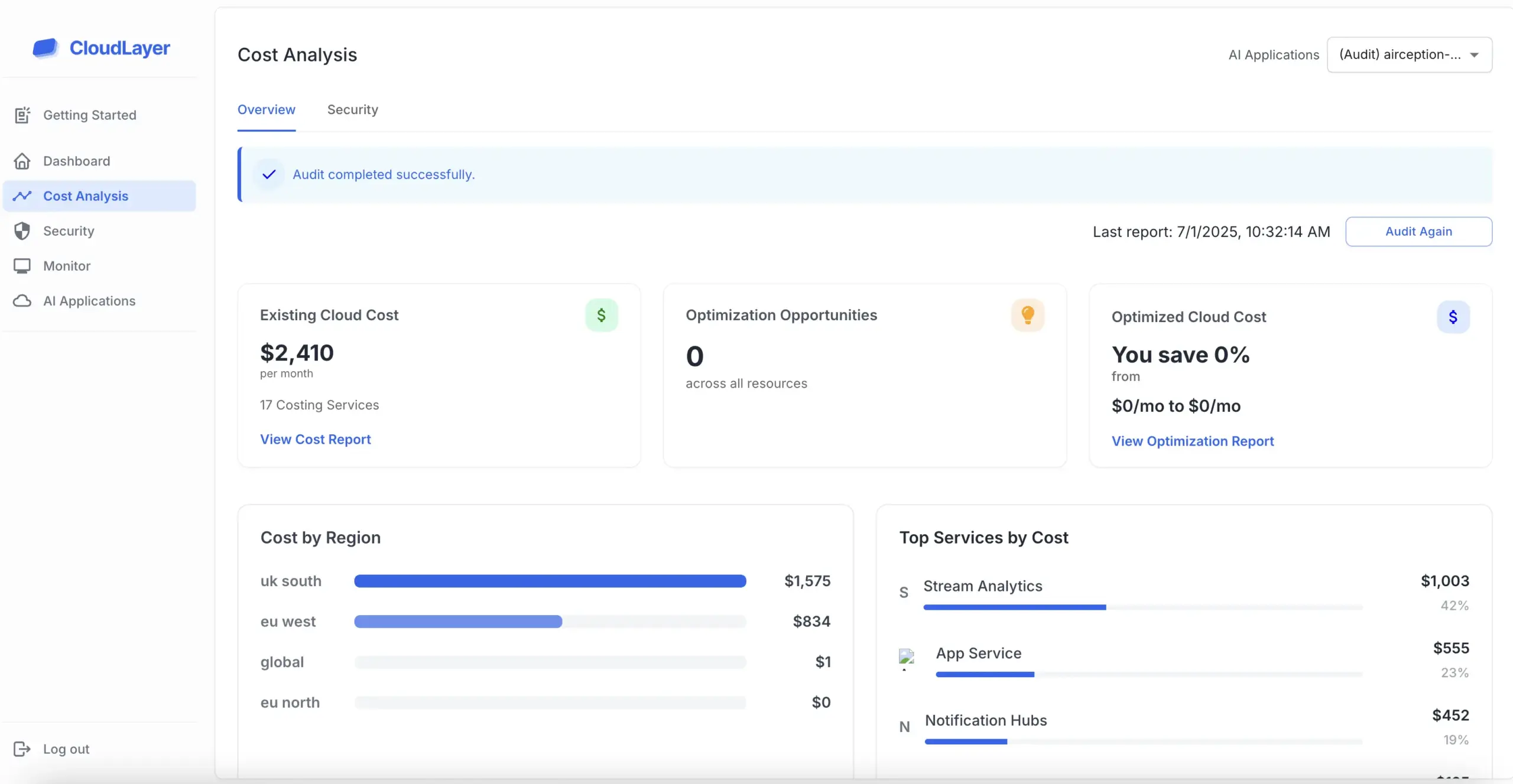
The primary purpose of pentesting is to identify and address vulnerabilities in a system before they can be exploited by cybercriminals. By conducting thorough assessments, organizations can understand their security posture and make informed decisions about necessary improvements.
Pentesting can be categorized into several types, each focusing on different aspects of security. Common types include network pentesting, web application pentesting, social engineering, and physical security assessments.
The pentesting process typically involves several phases, starting with planning and reconnaissance. Following this, the tester conducts scanning, gaining access, maintaining access, and finally, analysis and reporting.
Engaging in pentesting offers numerous benefits, including enhanced security, compliance with regulations, and improved risk management. Organizations that proactively address vulnerabilities can avoid costly data breaches and maintain their reputation.