SOC 2 requirements are based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy. Each of these criteria provides a framework for evaluating how well a company protects customer data.
1. Security: This criterion focuses on protecting systems against unauthorized access. It includes measures such as firewalls, intrusion detection systems, and access controls.
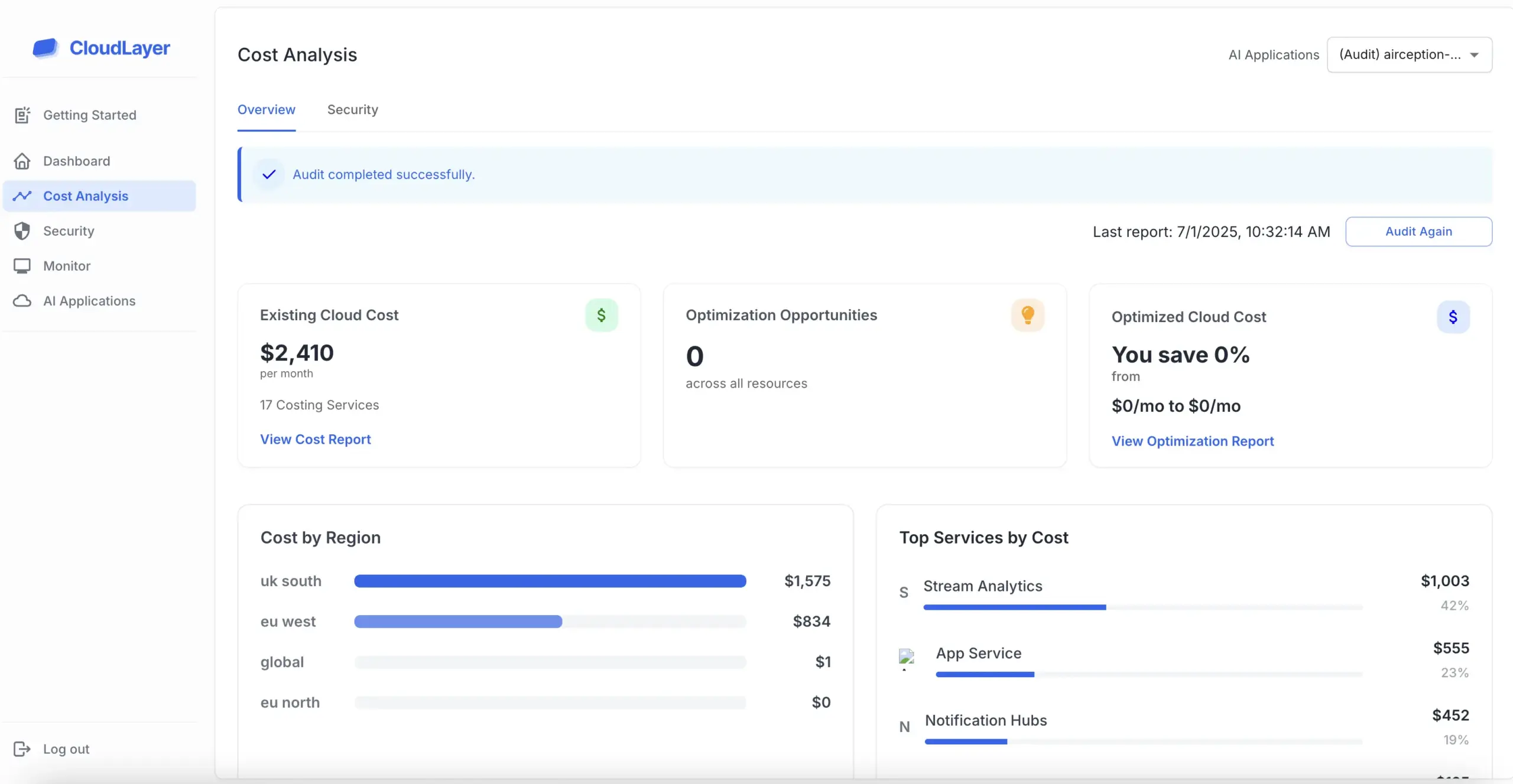
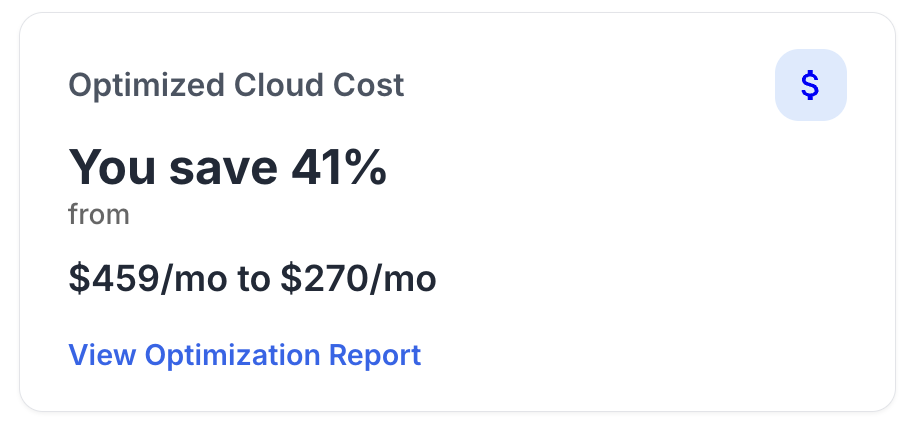
Meeting SOC 2 requirements is essential for building client trust and demonstrating commitment to data security. Clients are increasingly concerned about their data being mishandled, making compliance a significant competitive advantage.
To achieve SOC 2 compliance, organizations should start by conducting a thorough risk assessment to identify vulnerabilities. This assessment helps in understanding the current state of security measures and areas that require improvement.
Start using CloudLayer and experience a new level of efficiency.