SOC 2 compliance is vital for any organization that stores or processes data for clients, as it provides a structured approach to safeguarding personal and sensitive information. This compliance not only helps organizations to avoid data breaches and potential legal issues but also enhances their reputation in the marketplace.
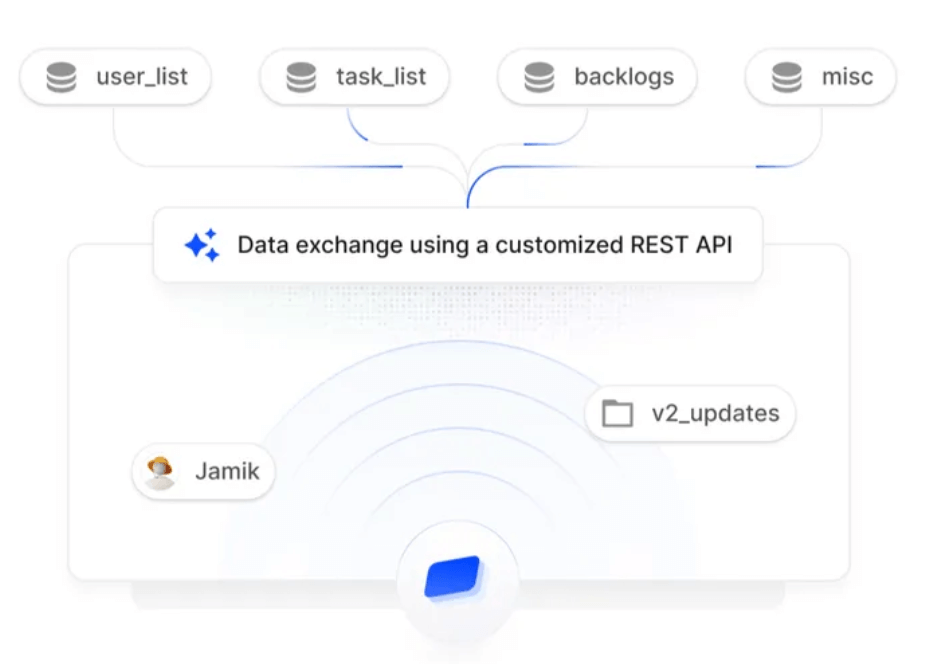
The SOC 2 framework revolves around five key trust service criteria: security, availability, processing integrity, confidentiality, and privacy. Each criterion addresses different aspects of data handling and protection, ensuring a holistic approach to compliance.
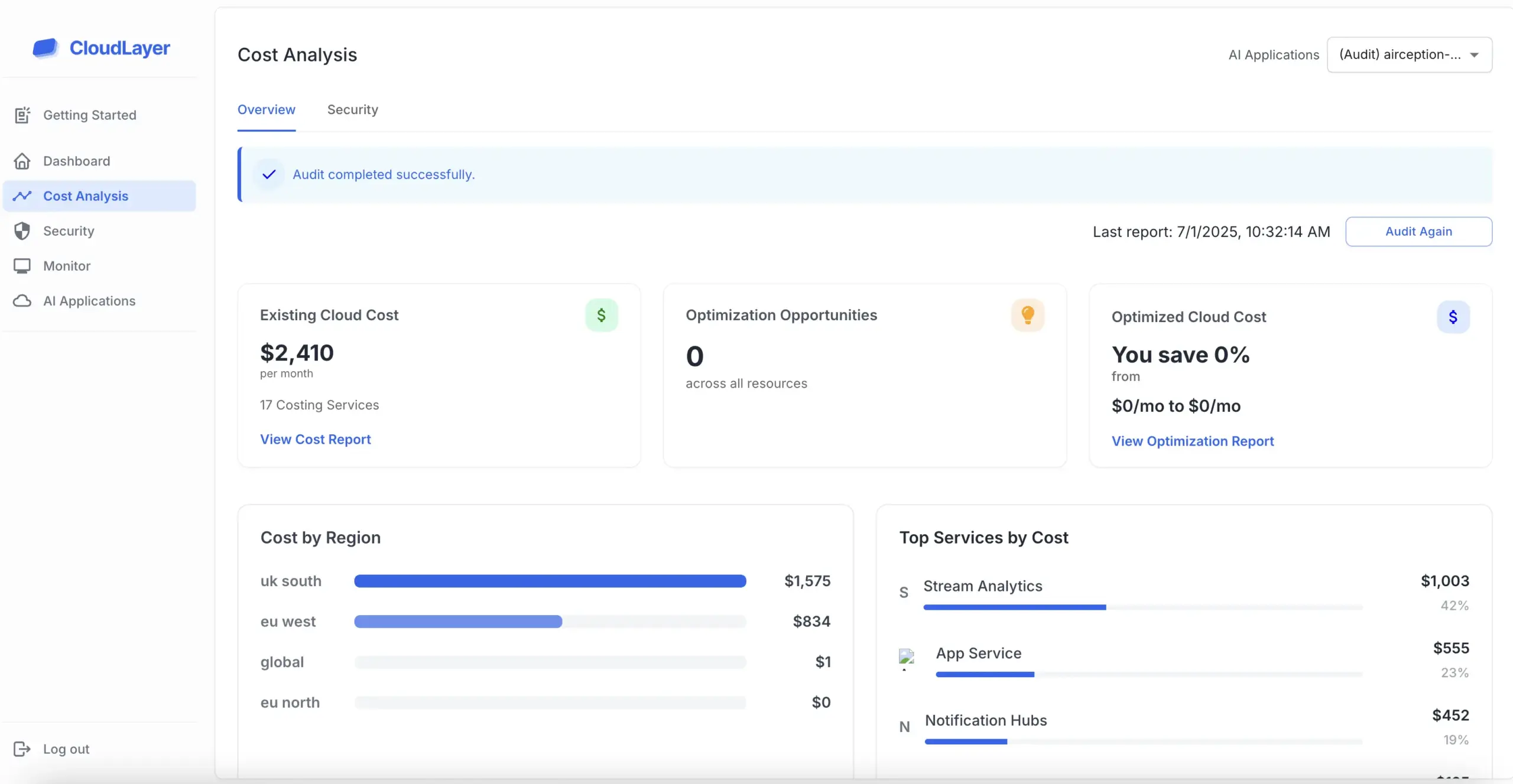
To achieve SOC 2 compliance, organizations must undergo a thorough audit conducted by an independent third-party auditor. This process involves evaluating existing security measures and identifying gaps that need addressing to meet compliance requirements.
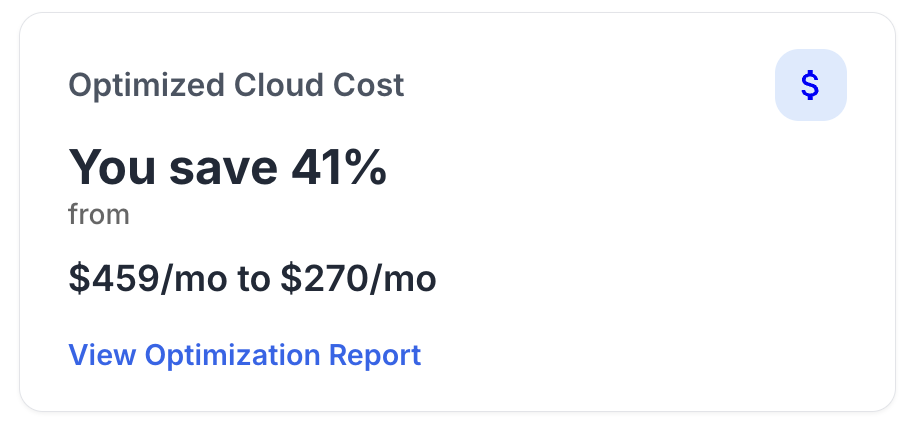
Obtaining SOC 2 certification offers numerous benefits, including increased customer trust and improved operational efficiency. Companies with this certification can differentiate themselves in a competitive market, showcasing their commitment to data security and privacy.
Start using CloudLayer and experience a new level of efficiency.