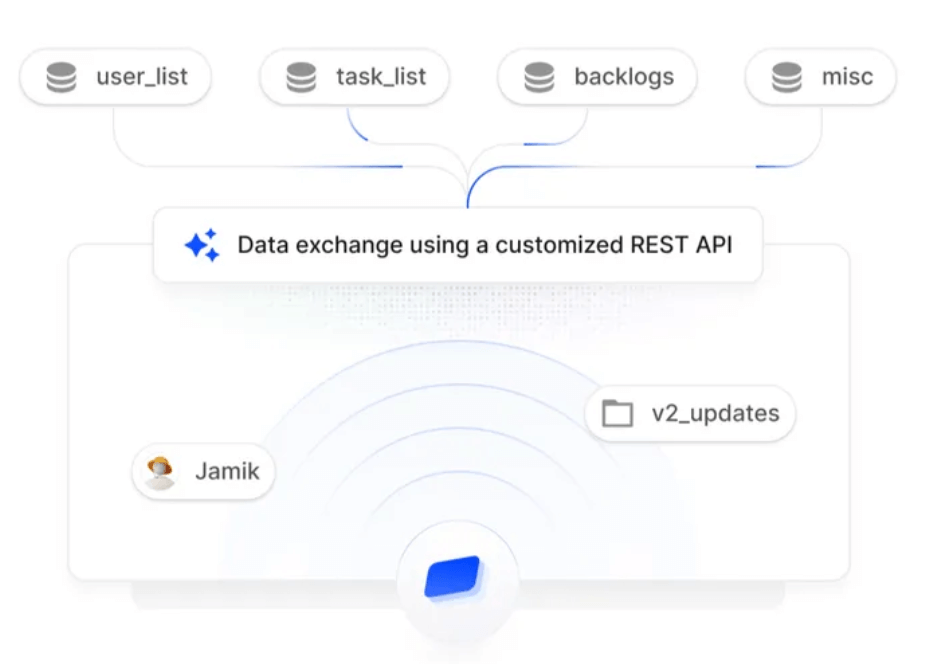
A SOC 2 report consists of various components that collectively assess how well a service organization manages data to protect the interests of its clients. The five Trust Services Criteria — security, availability, processing integrity, confidentiality, and privacy — form the backbone of the evaluation.
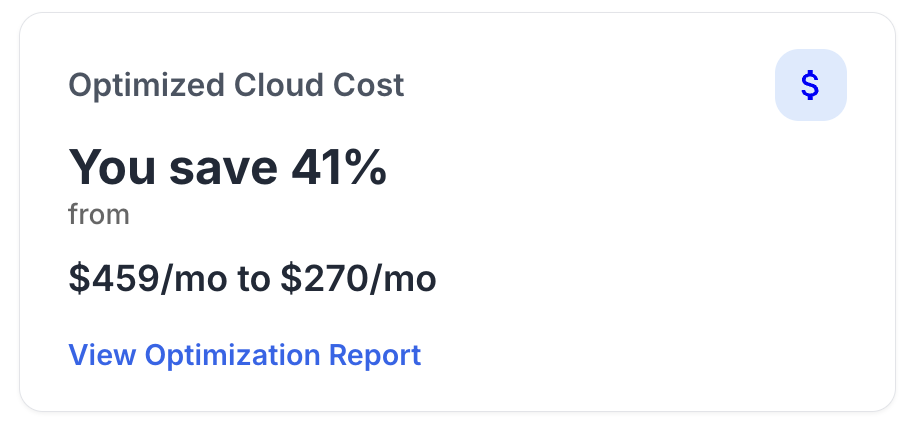
There are two types of SOC 2 reports: Type I and Type II. Type I reports evaluate the design of controls at a specific point in time, while Type II reports assess the operational effectiveness of these controls over a defined period.
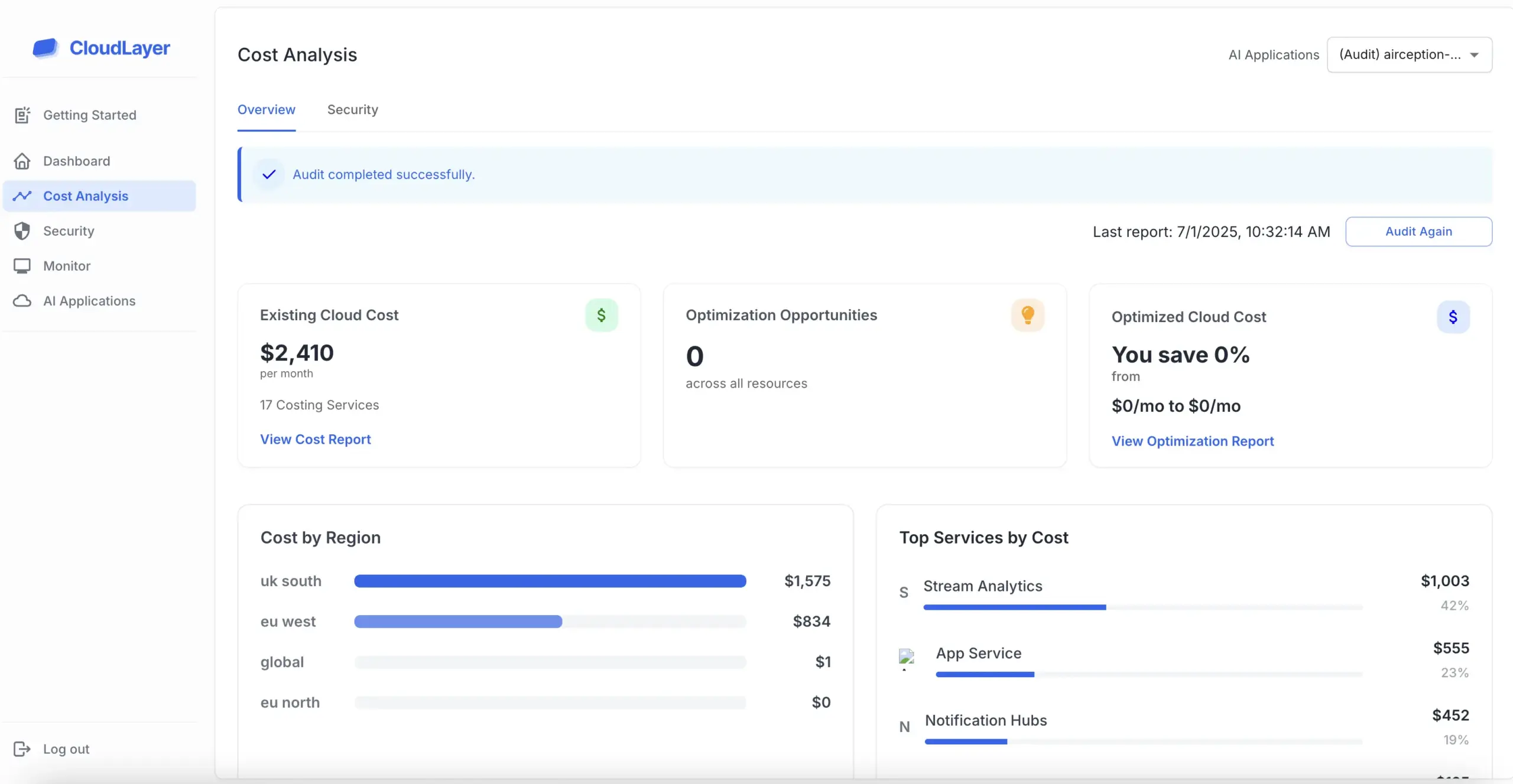
SOC 2 reports are vital for building trust with existing and potential clients. By providing transparency regarding data security practices, organizations can differentiate themselves in a crowded marketplace and attract new customers.
To obtain a SOC 2 report, an organization must undergo an audit conducted by a certified public accountant (CPA). This process involves a thorough examination of the organization’s controls and practices related to the Trust Services Criteria.
Start using CloudLayer and experience a new level of efficiency.