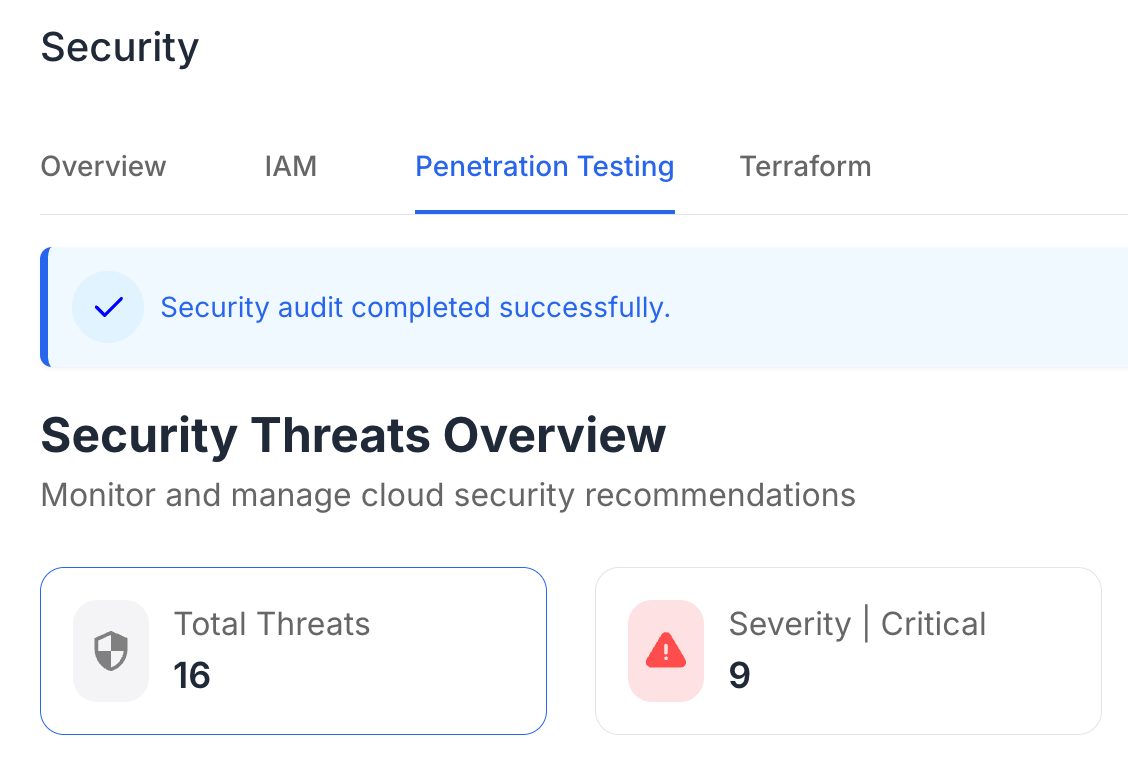
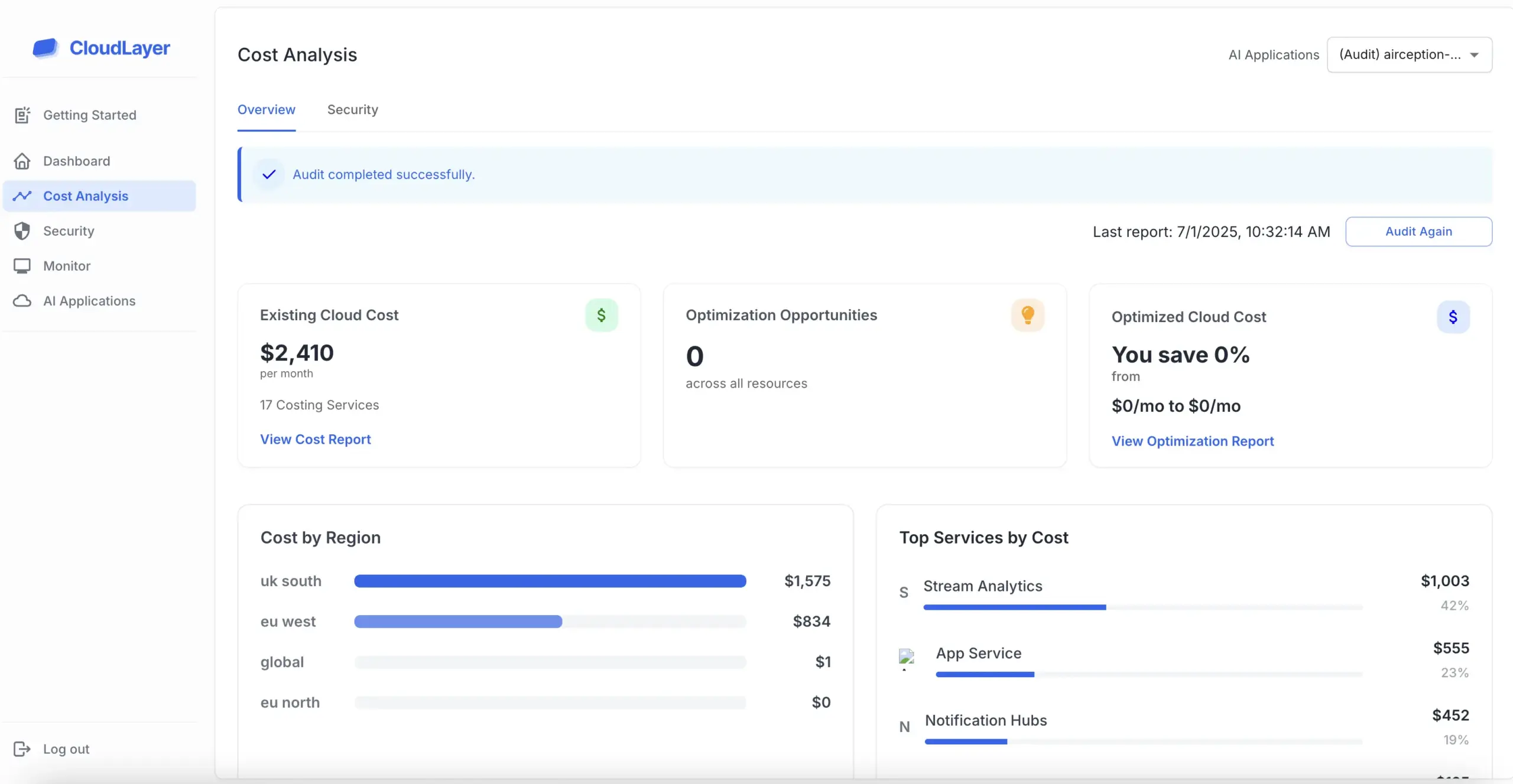
SOC 2 compliance is a rigorous auditing process that evaluates the effectiveness of a service organization’s controls related to data security. This compliance is particularly relevant for technology and cloud computing companies that handle sensitive customer information.
Achieving SOC 2 compliance is crucial for businesses looking to foster trust with clients and partners. It serves as a benchmark for security practices and assures stakeholders that an organization prioritizes the protection of their data.
The SOC 2 framework is built around five trust service criteria: security, availability, processing integrity, confidentiality, and privacy. Each of these components plays a vital role in ensuring that organizations implement the necessary controls to protect customer data effectively.
The journey to SOC 2 compliance involves several key steps, beginning with a thorough risk assessment to identify potential vulnerabilities. Organizations must then implement the appropriate controls, regularly monitor their effectiveness, and prepare for an external audit.