Misconfigured IAM roles are a top security risk. We audit and optimize your policies, permissions, and user groups to ensure least-privilege access. Gain tighter control over who can access what, and why.
Excessive permissions often go unnoticed and create vulnerabilities. Our analysis identifies over-privileged users, roles, and service accounts. We help you clean up access rights to prevent lateral movement and privilege escalation.
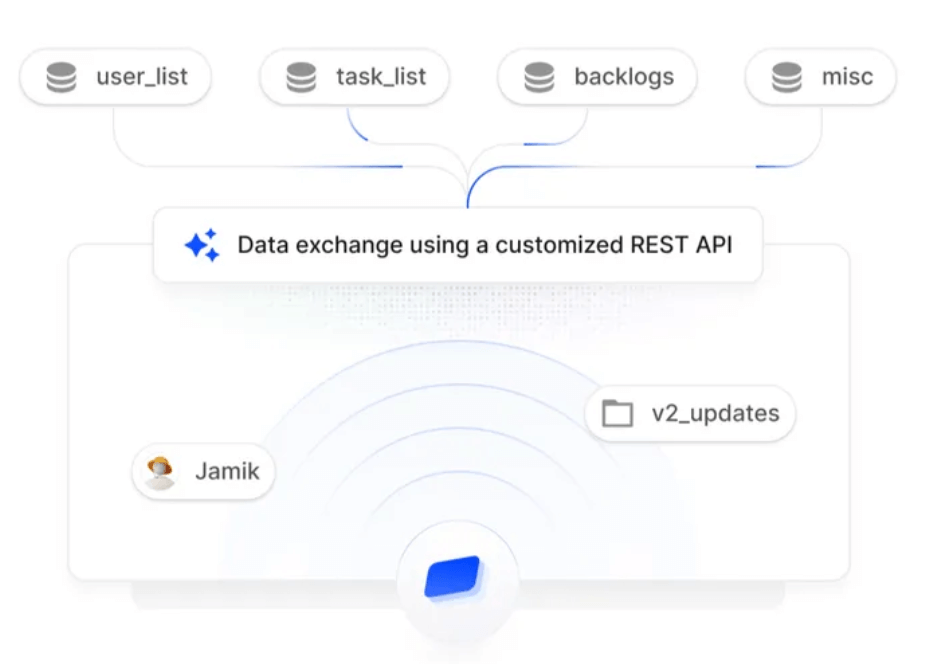
Staying secure means following IAM best practices aligned with standards like CIS, NIST, or ISO. We help you enforce MFA, rotate credentials, and implement audit logging. Strengthen your IAM posture while meeting regulatory requirements.
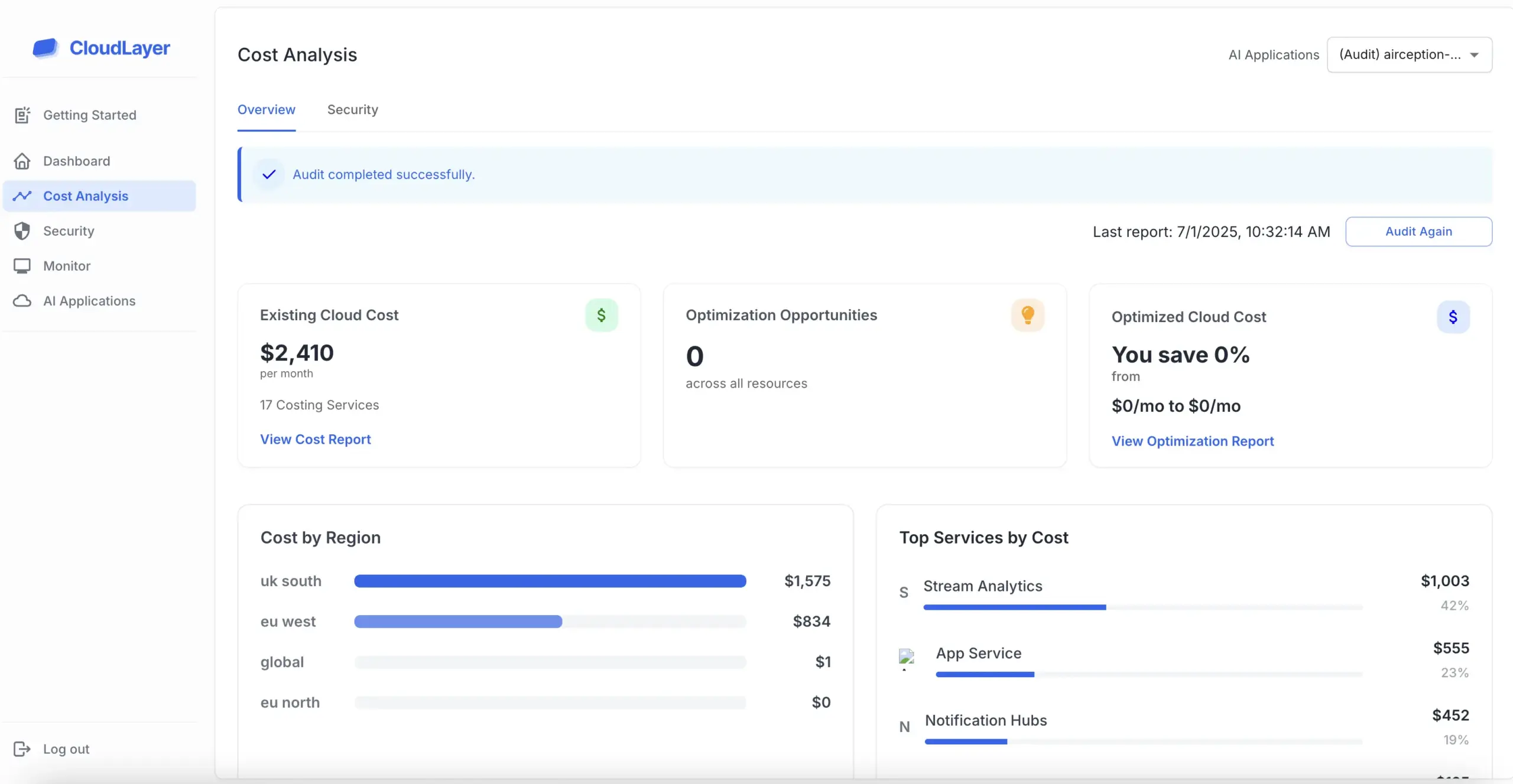
IAM configurations can drift over time, introducing new risks. We provide continuous monitoring, anomaly detection, and alerting for IAM activities. Stay protected with proactive identity security management.
Start using CloudLayer and experience a new level of efficiency.