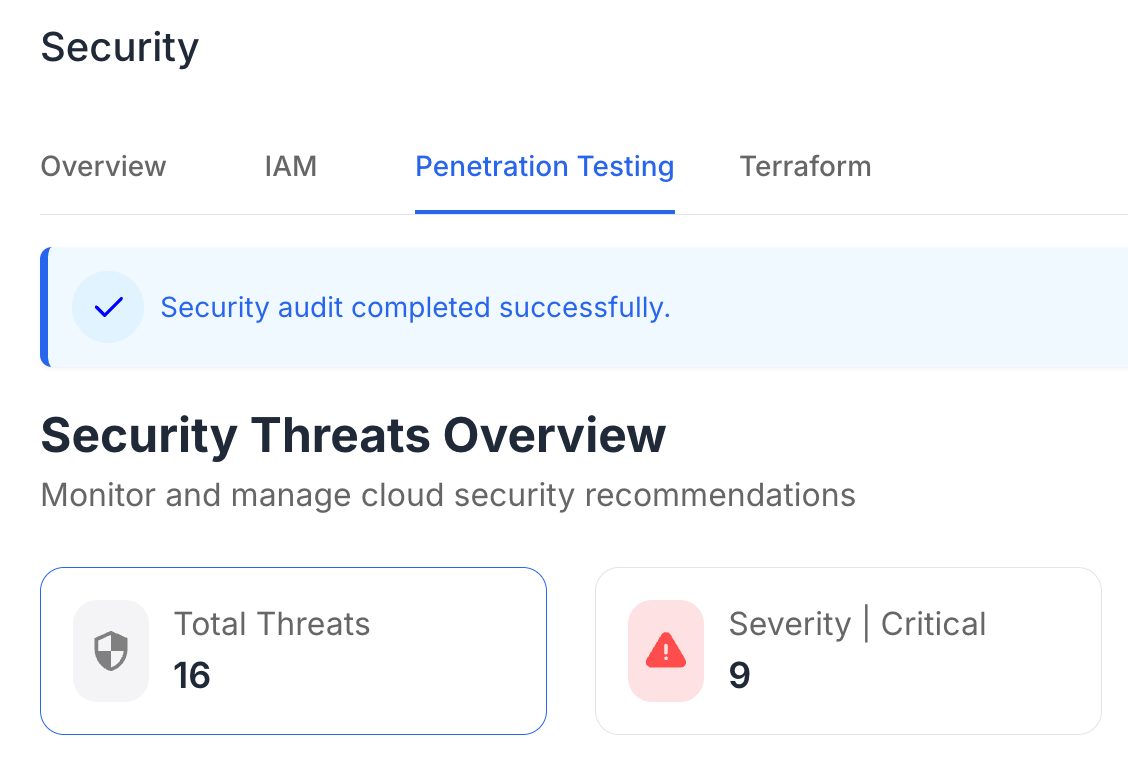
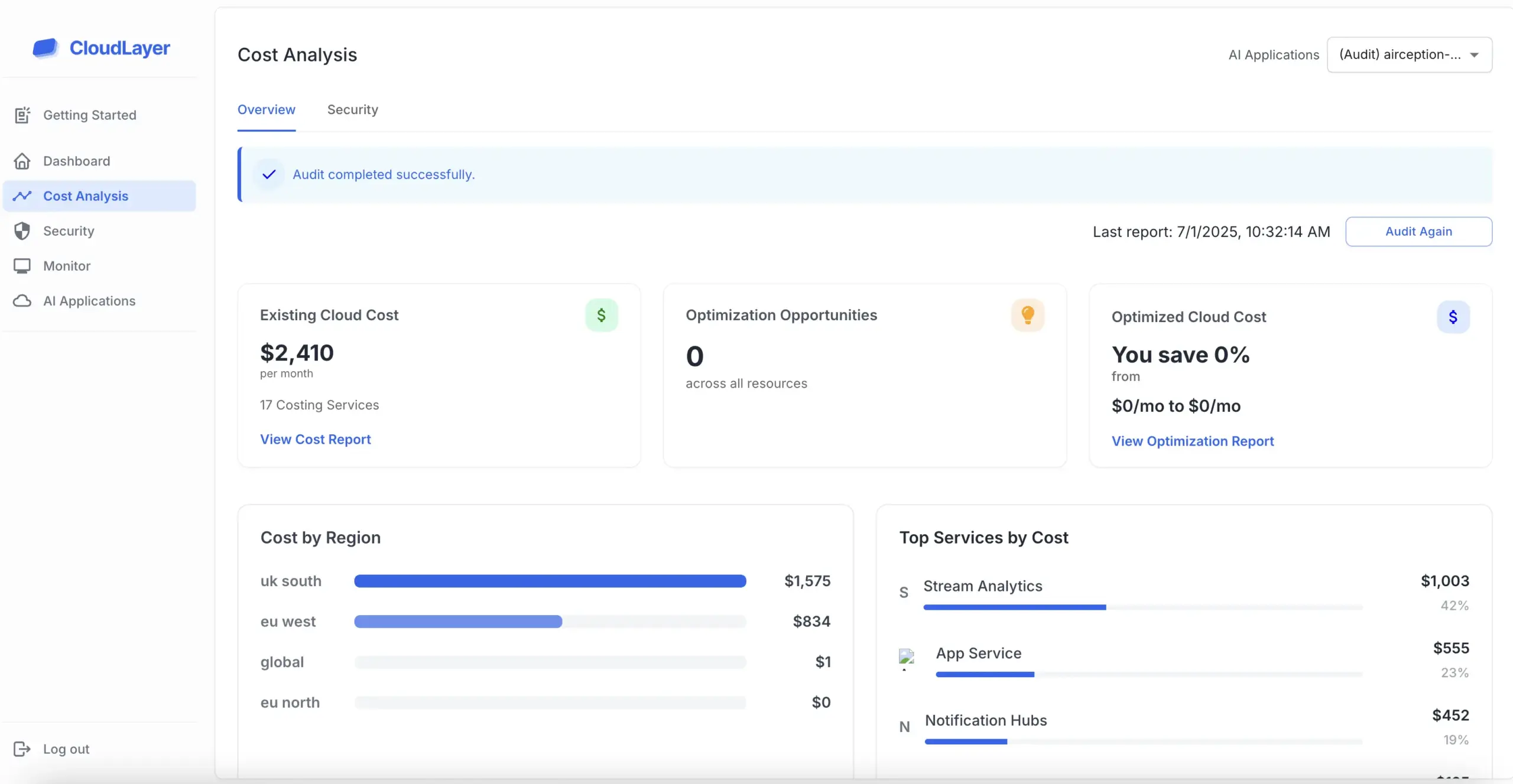
Penetration testing, also known as ethical hacking, involves simulating attacks on a computer system, network, or web application. The goal is to discover vulnerabilities that could be exploited by malicious hackers.
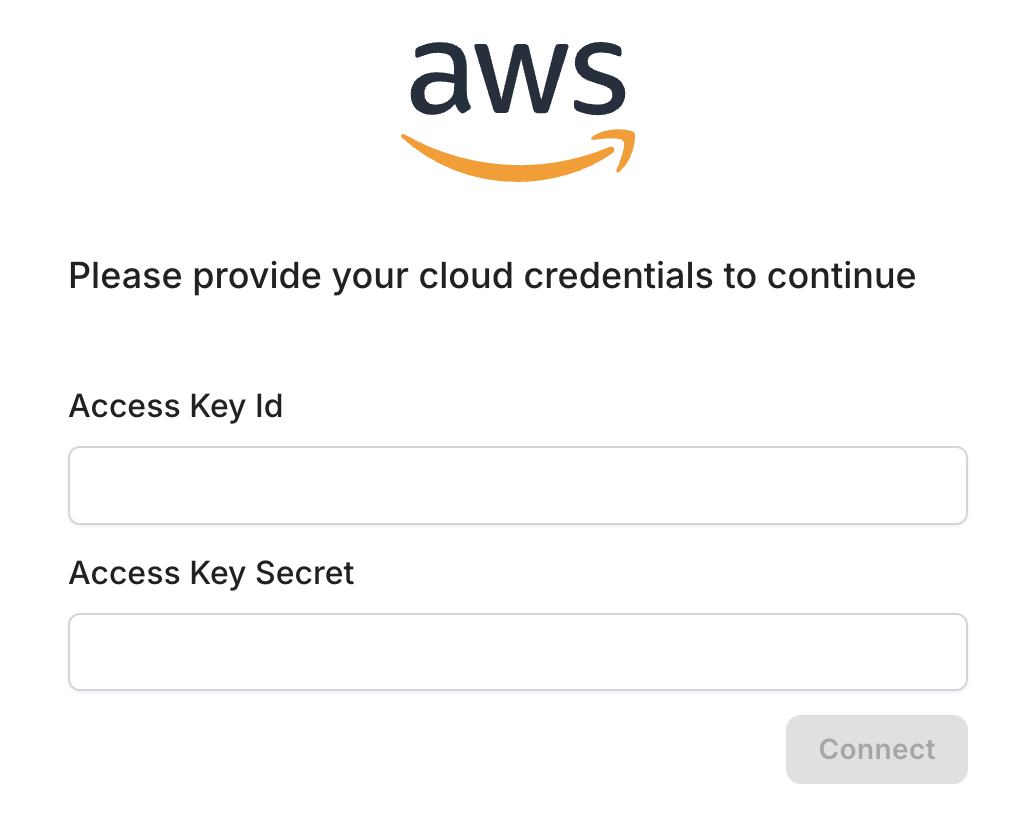
The penetration testing process is typically divided into several phases: planning, scanning, gaining access, maintaining access, and analysis. Each phase plays a crucial role in comprehensively assessing security.
The first phase involves defining the scope and objectives of the test. Ethical hackers gather information about the target system to understand potential vulnerabilities and entry points.
In this phase, tools are used to identify live hosts, open ports, and services running on the target system. Scanning helps in mapping the attack surface and identifying vulnerabilities that need further investigation.