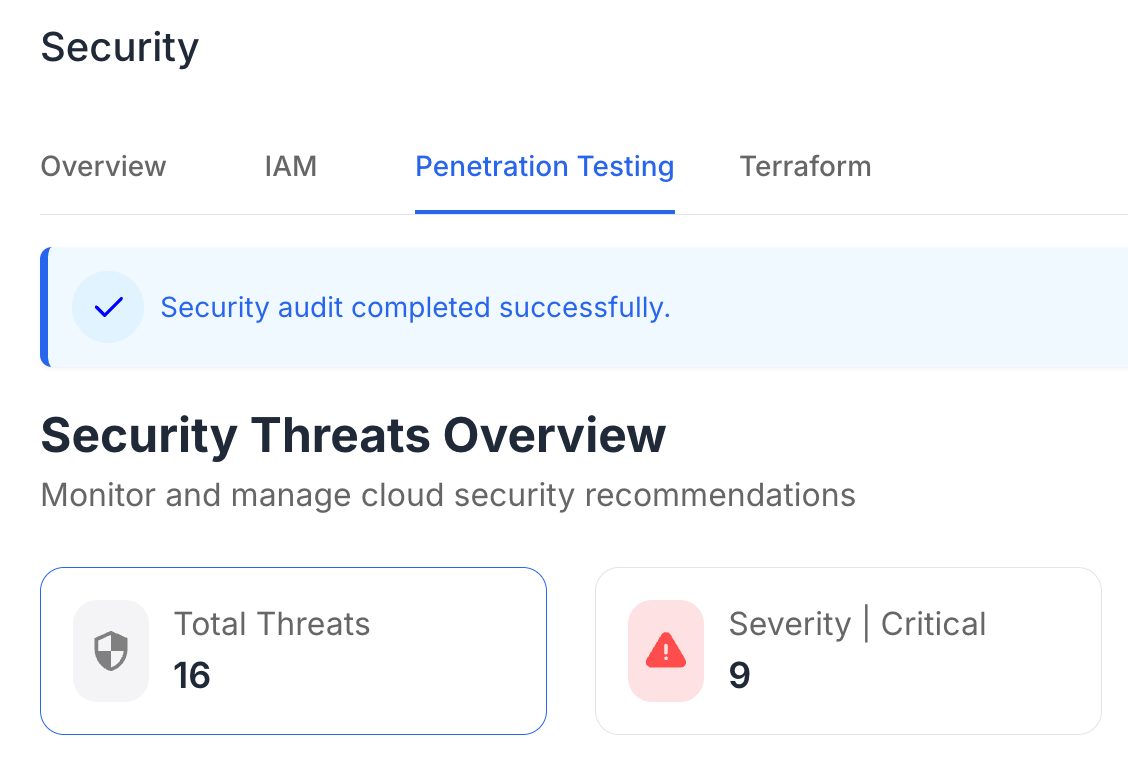
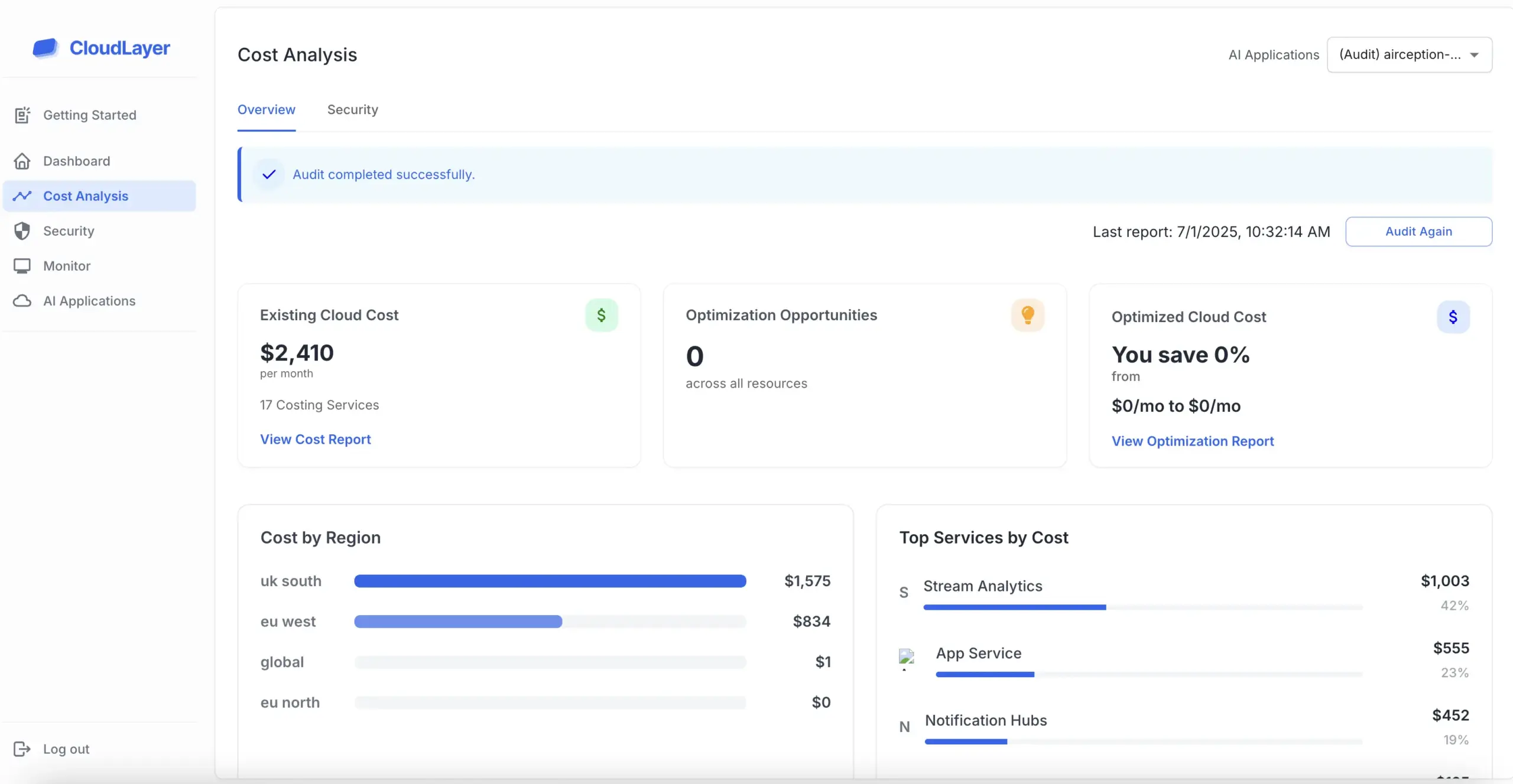
Cyber security in cloud computing encompasses the strategies and technologies used to protect cloud-based systems and data. It involves safeguarding against threats such as data breaches, unauthorized access, and service disruptions.
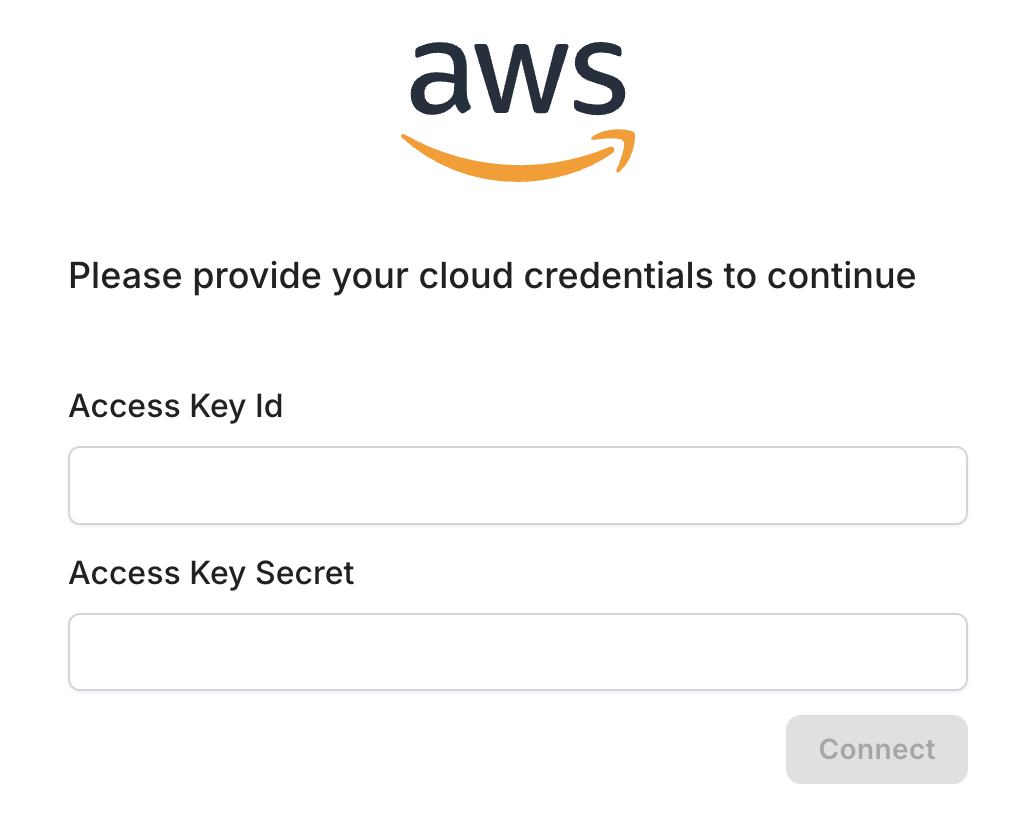
Several threats pose risks to cloud security, including data breaches and account hijacking. Additionally, misconfigured cloud settings and insider threats can significantly compromise the integrity of cloud services.
Implementing best practices is vital for enhancing cyber security in cloud computing. Regularly updating software, employing strong authentication methods, and conducting security audits can mitigate risks effectively.
Compliance with regulations and standards is crucial for ensuring cloud security. Organizations must stay informed about regulations such as GDPR and HIPAA to protect sensitive information and avoid legal repercussions.