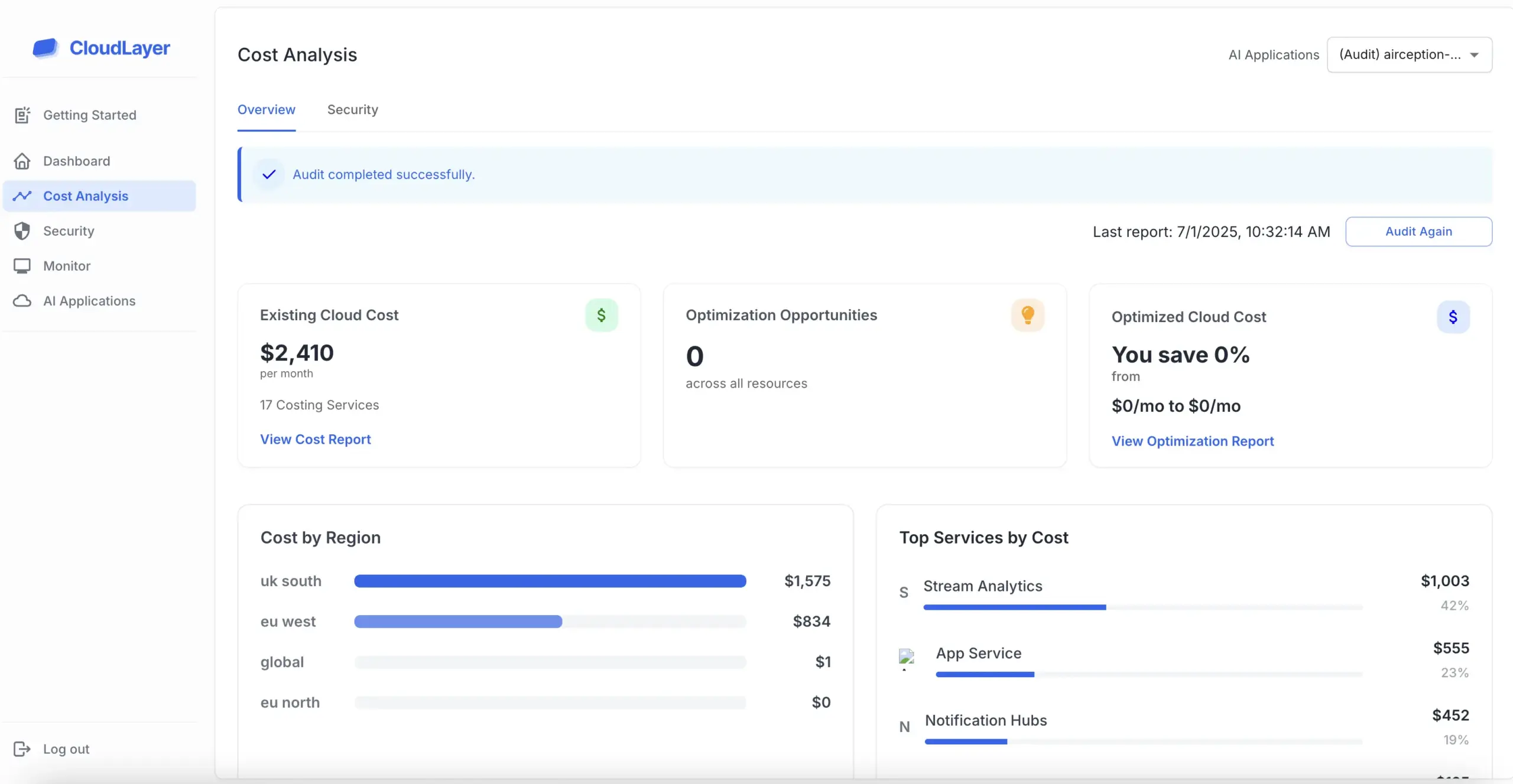
A SOC 2 audit, developed by the American Institute of CPAs (AICPA), focuses on a service organization’s controls related to data security, availability, processing integrity, confidentiality, and privacy. This type of audit is particularly relevant for technology and cloud computing companies that handle customer data.
SOC 2 audits are essential for establishing trust between service providers and their clients. By undergoing a SOC 2 audit, organizations can demonstrate their commitment to maintaining robust security practices and protecting sensitive information.
The SOC 2 audit process includes several key components, such as the Trust Services Criteria (TSC), which outline the principles that organizations must adhere to. These criteria serve as a framework for evaluating the effectiveness of the organization’s controls.
Preparation is crucial for a successful SOC 2 audit. Organizations should conduct a thorough assessment of their current security practices and identify gaps that need to be addressed before the audit takes place.
Start using CloudLayer and experience a new level of efficiency.