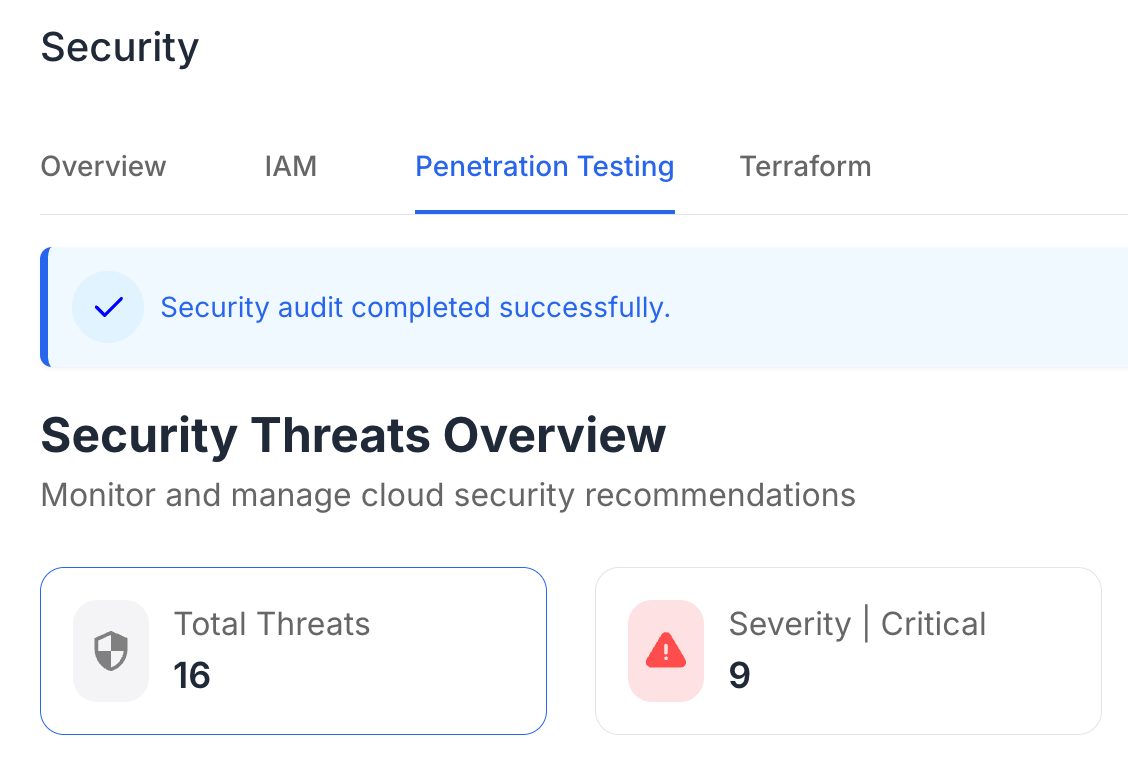
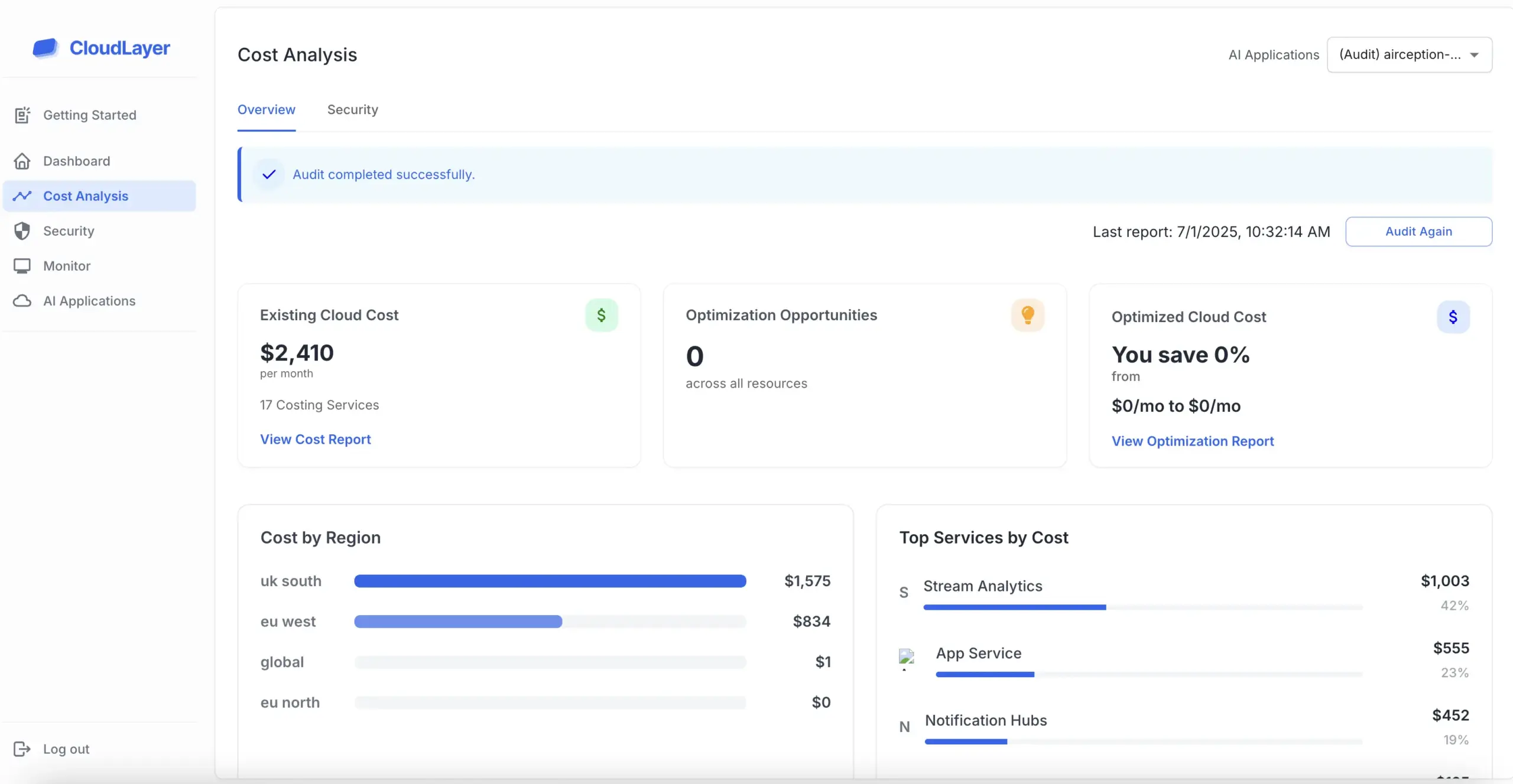
Insecure identity and access setups are the main reason behind AWS security incidents. We assess and refine IAM policies, roles, and permissions to uphold least-privilege access. Guarantee that only authorized users and systems gain entry—no more.
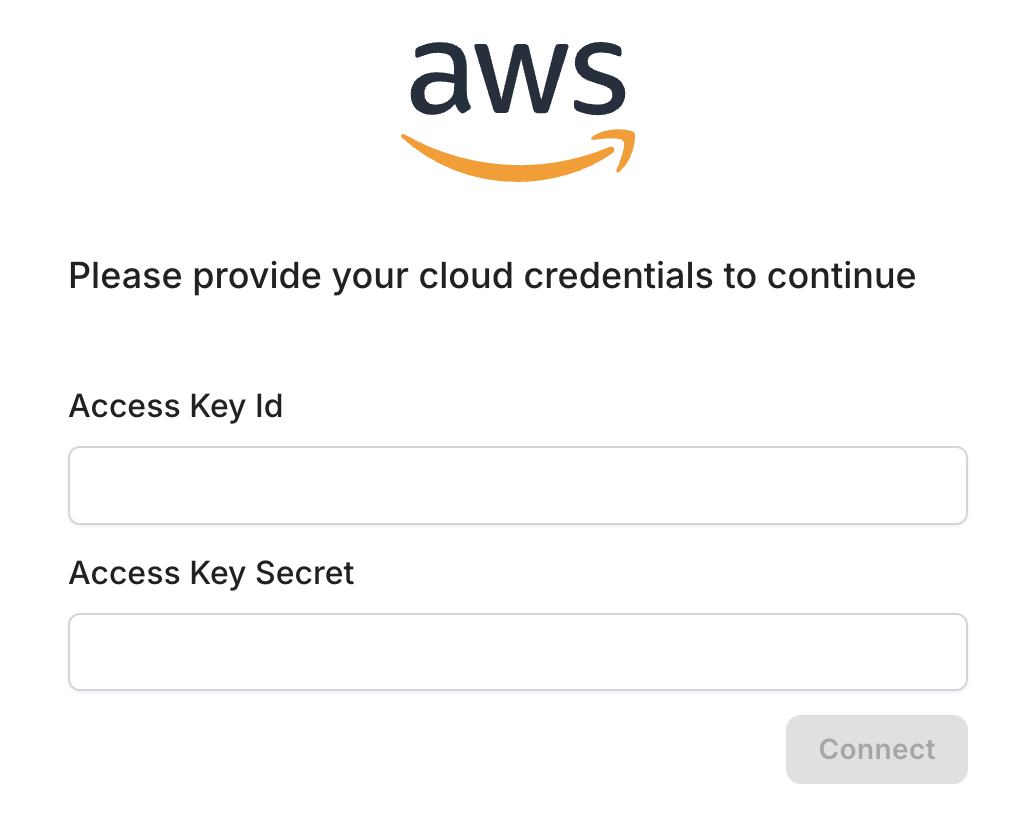
Security risks often hide in misconfigured services like S3, EC2, or RDS. We scan your environment for exposures, including public buckets, open ports, and weak encryption. Fix issues fast to stay protected and compliant.
We synchronize your environment with AWS-endorsed security frameworks such as the Well-Architected Framework and CIS Benchmarks. From monitoring and logging to managing keys, we assist you in constructing a robust cloud security base.
Security threats evolve, and your protection should too. We implement continuous monitoring, alerting, and automated responses using AWS tools like CloudTrail, GuardDuty, and Config. Stay ahead of threats with real-time cloud security.