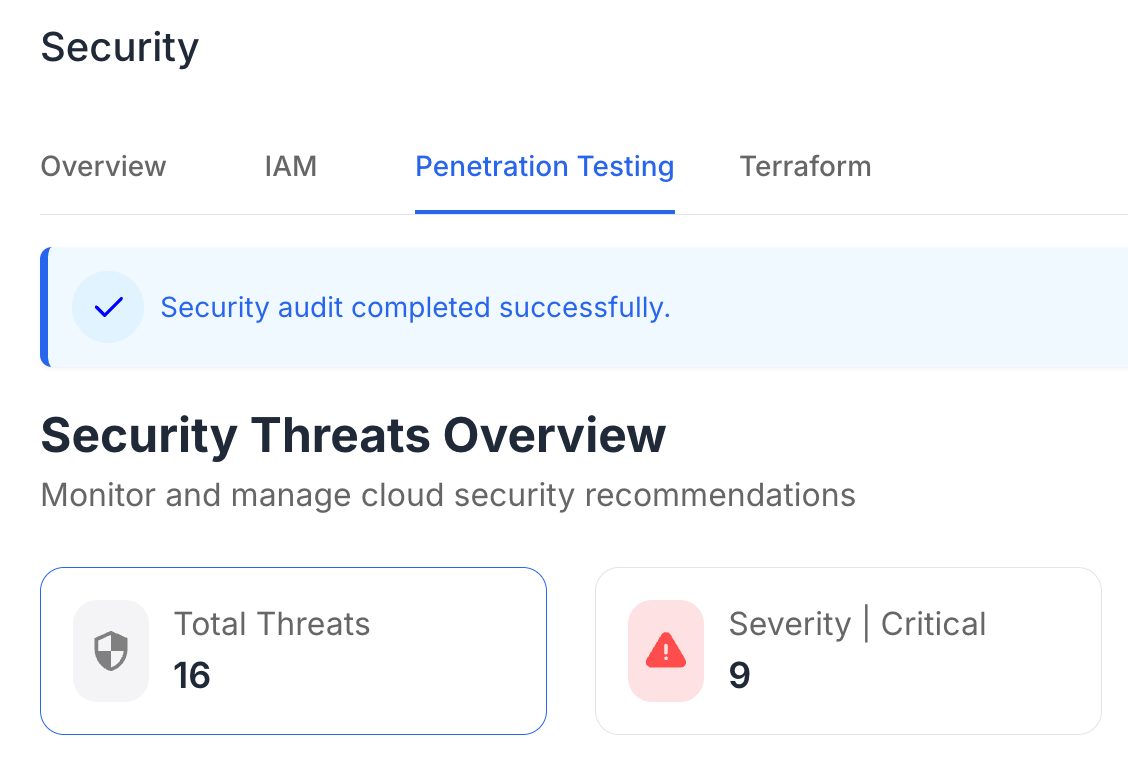
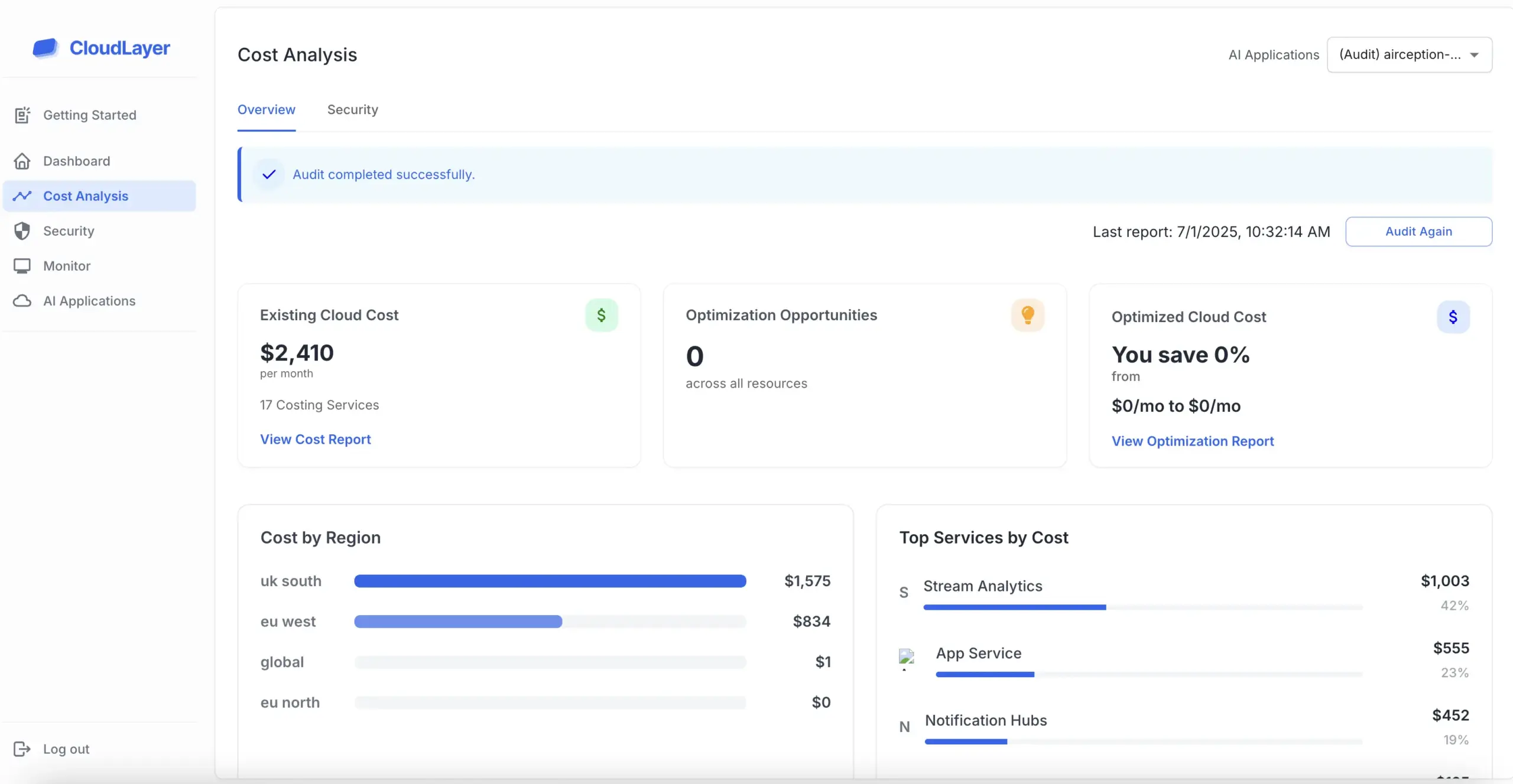
HIPAA, the Health Insurance Portability and Accountability Act, establishes national standards for the protection of patient health information. Compliance with HIPAA is crucial for healthcare providers to avoid hefty fines and maintain patient trust.
A thorough risk assessment is the foundation of HIPAA compliance. This process identifies vulnerabilities in your IT systems and provides insights into how to mitigate potential risks to patient data.
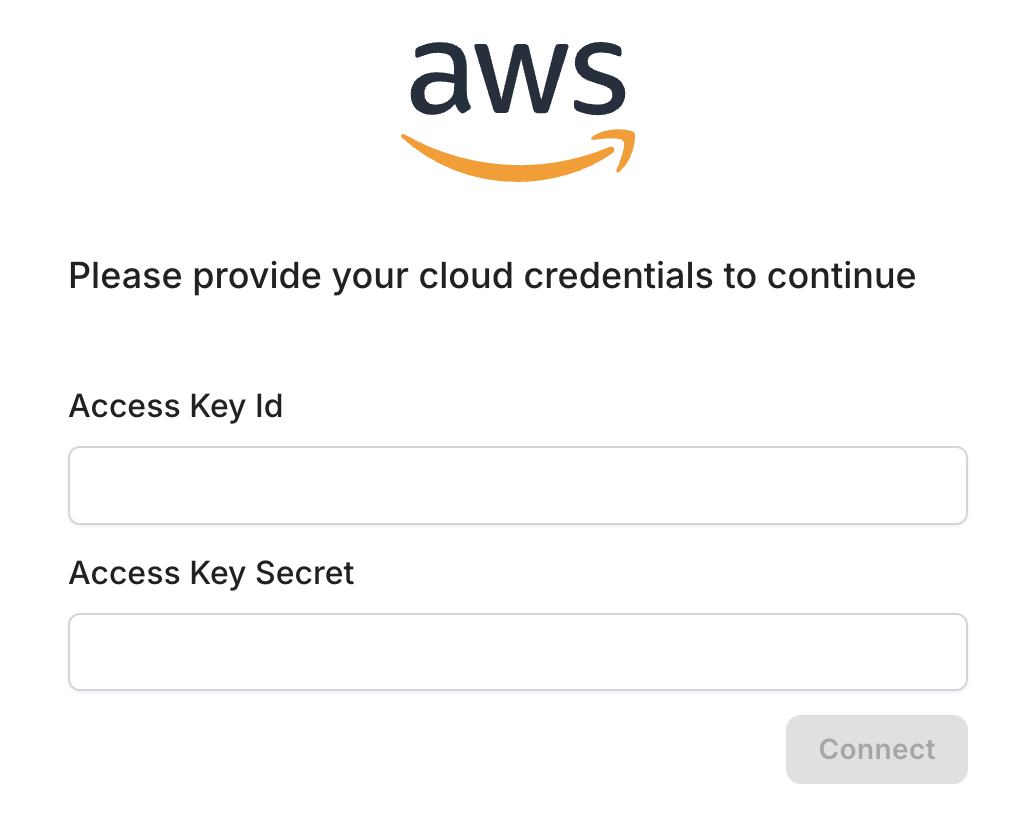
Access controls are vital for safeguarding electronic protected health information (ePHI). Ensure that only authorized personnel have access to sensitive data through robust authentication methods.
Data encryption is a critical measure for protecting ePHI during transmission and storage. Implementing encryption technologies ensures that even if data is compromised, it remains unreadable to unauthorized users.