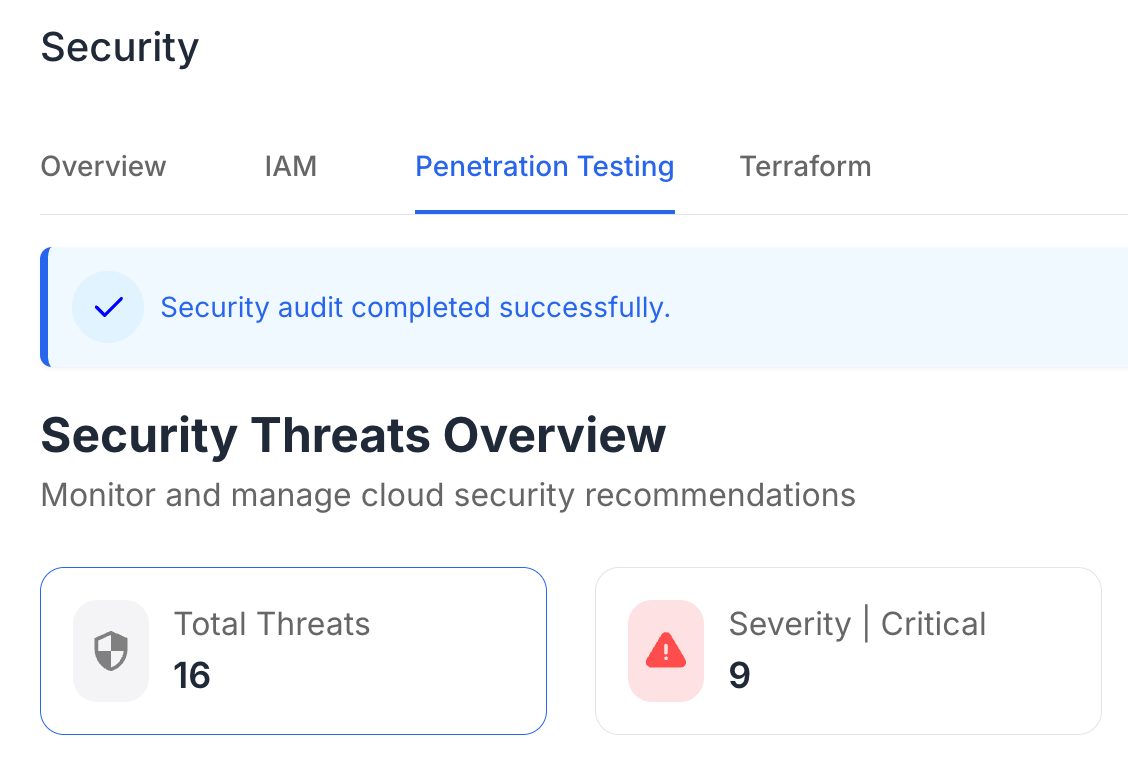
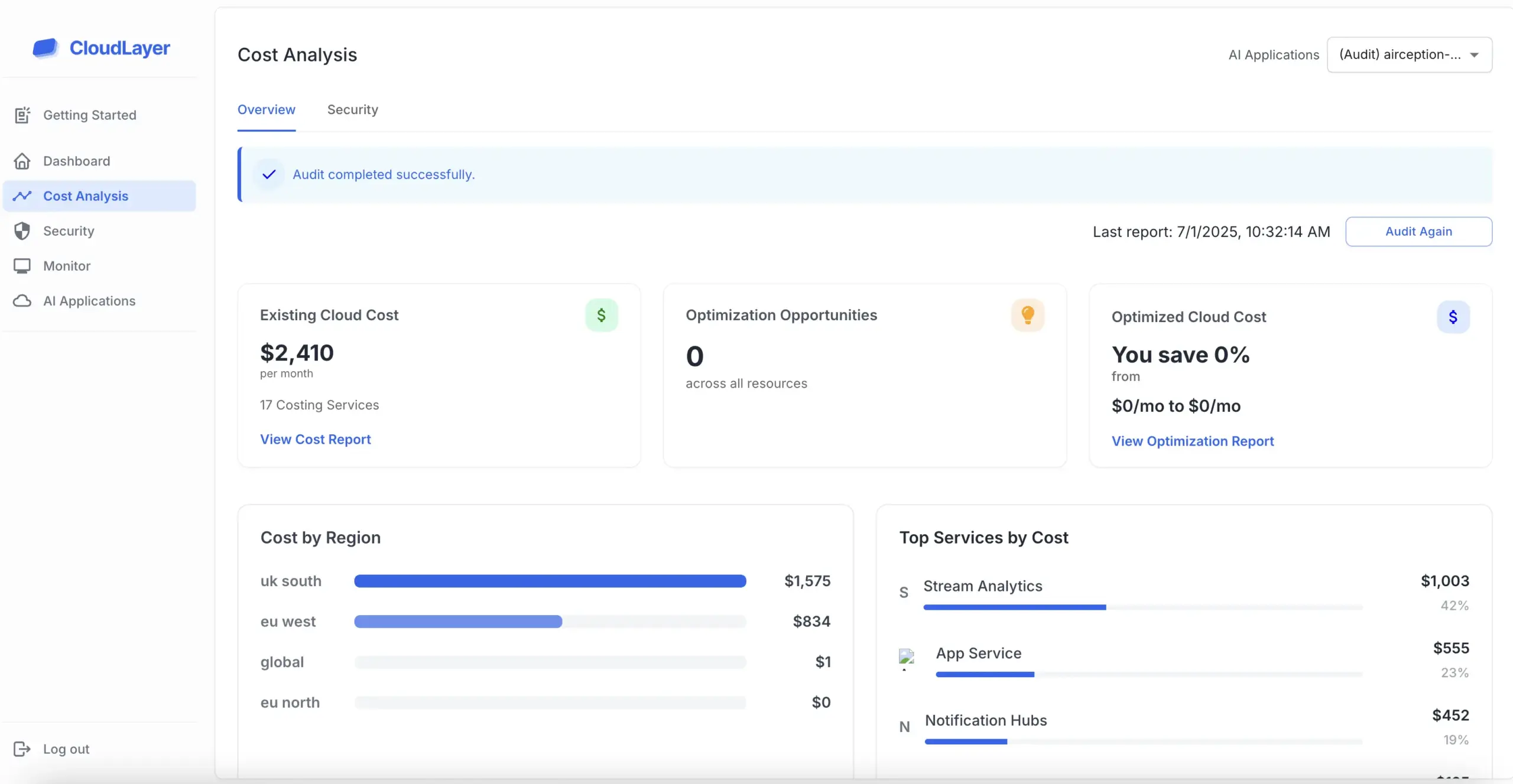
Penetration testing is essential for identifying potential security flaws in software applications. By mimicking the tactics of malicious hackers, organizations can uncover vulnerabilities that may otherwise go unnoticed.
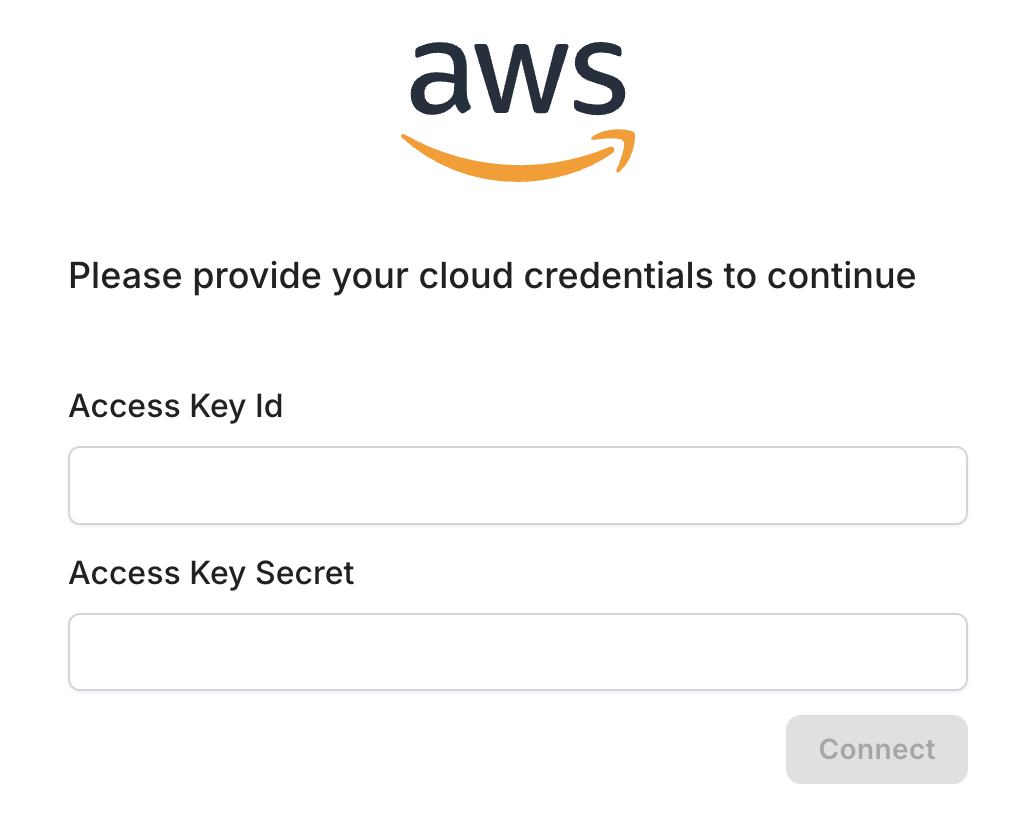
There are several types of penetration testing, each tailored to different needs and environments. The most common types include external, internal, and web application testing.
The penetration testing process typically involves several key phases: planning, scanning, gaining access, maintaining access, and analysis. Each phase is crucial for ensuring a comprehensive evaluation of security measures.
To maximize the effectiveness of penetration testing, organizations should follow best practices, including defining clear objectives and ensuring thorough documentation. Regular testing helps to keep security measures updated and relevant.