SOC 2 compliance is part of the System and Organization Controls (SOC) framework established by the American Institute of CPAs (AICPA). It specifically focuses on service organizations that handle customer data, ensuring they have adequate measures to protect that data.
For many organizations, achieving SOC 2 compliance is essential for gaining a competitive edge. Clients and partners expect assurance that their data is handled securely, and compliance can serve as a testament to your organization’s commitment to risk management and data protection.
SOC 2 compliance is evaluated based on five key trust service criteria. These include security, which focuses on protecting against unauthorized access, availability, which ensures systems are operational and accessible, processing integrity, confidentiality, and privacy, all of which safeguard customer data and personal information.
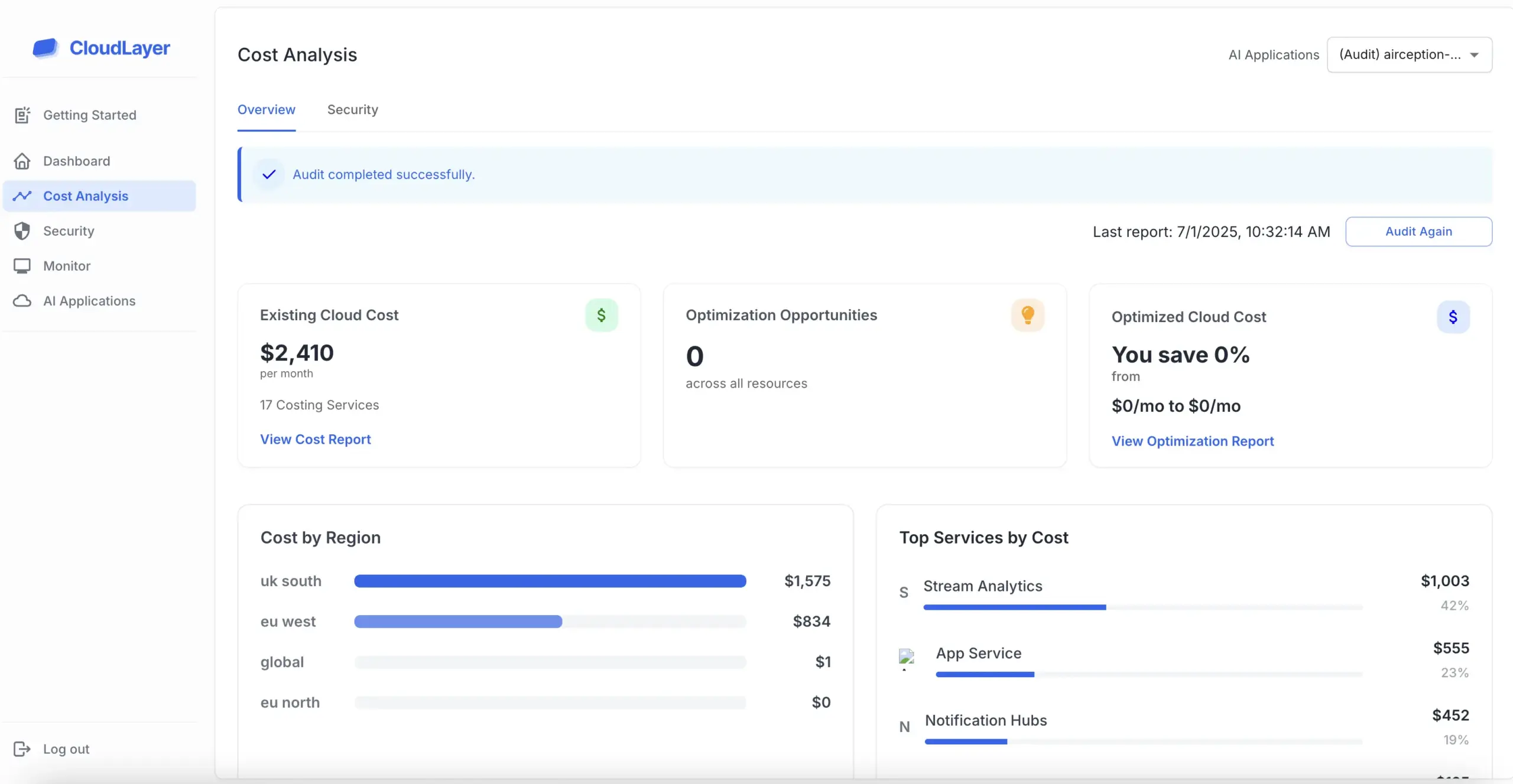
Achieving SOC 2 compliance involves several key steps. Organizations must first assess their current practices and identify gaps in their security measures, followed by implementing necessary controls and documentation to meet the SOC 2 criteria.
Start using CloudLayer and experience a new level of efficiency.