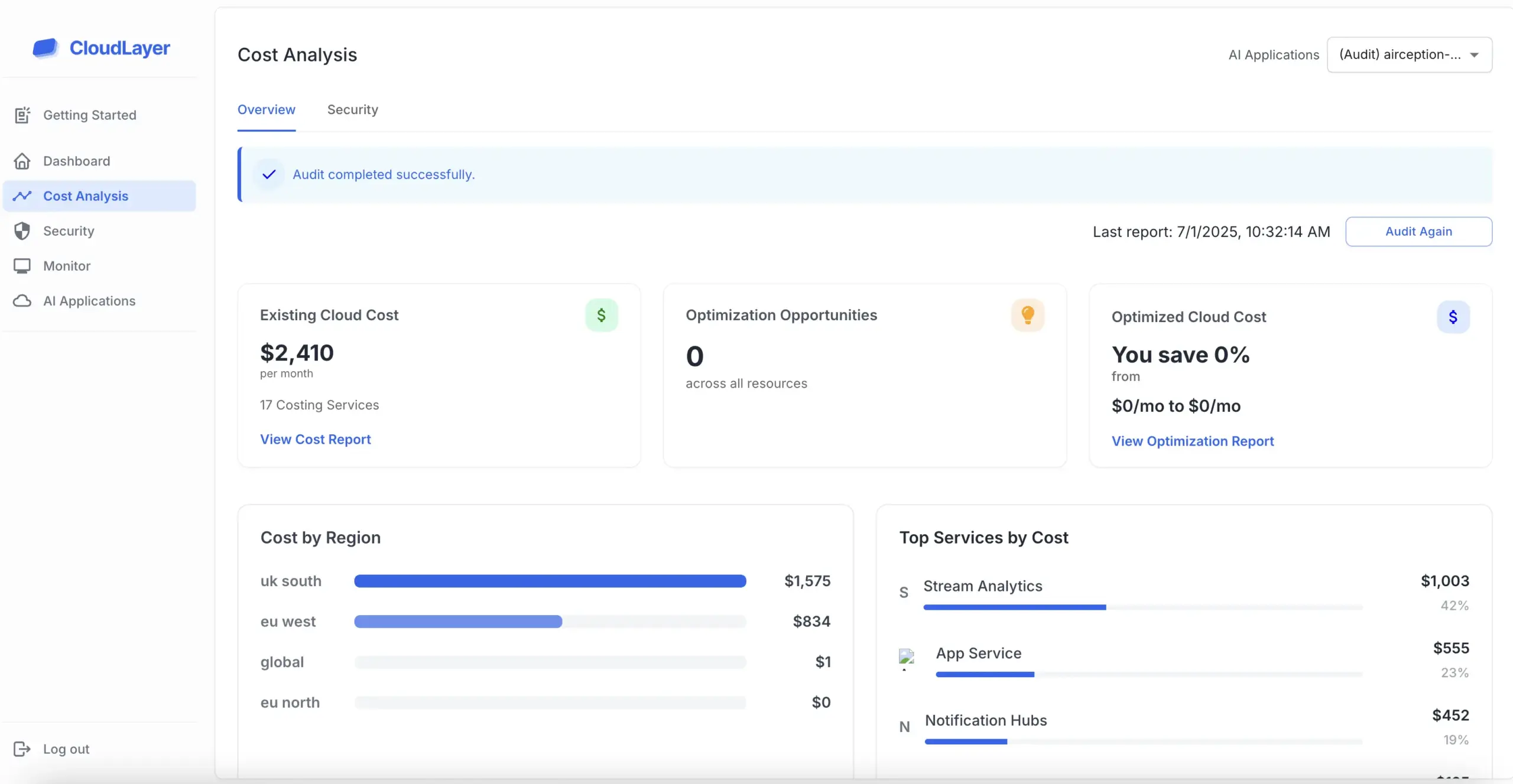
SOC 2, or System and Organization Controls 2, is a framework designed to ensure that service providers securely manage data to protect the privacy of their clients. Developed by the American Institute of CPAs (AICPA), it focuses on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
Achieving SOC 2 compliance is vital for organizations that handle sensitive data as it demonstrates a commitment to data security and integrity. Clients often require SOC 2 reports to ensure that their data is in safe hands, making compliance a competitive advantage.
SOC 2 compliance revolves around the implementation of effective controls and processes that adhere to the trust service criteria. Organizations must develop robust security measures, conduct regular risk assessments, and maintain documentation to demonstrate their adherence to these standards.
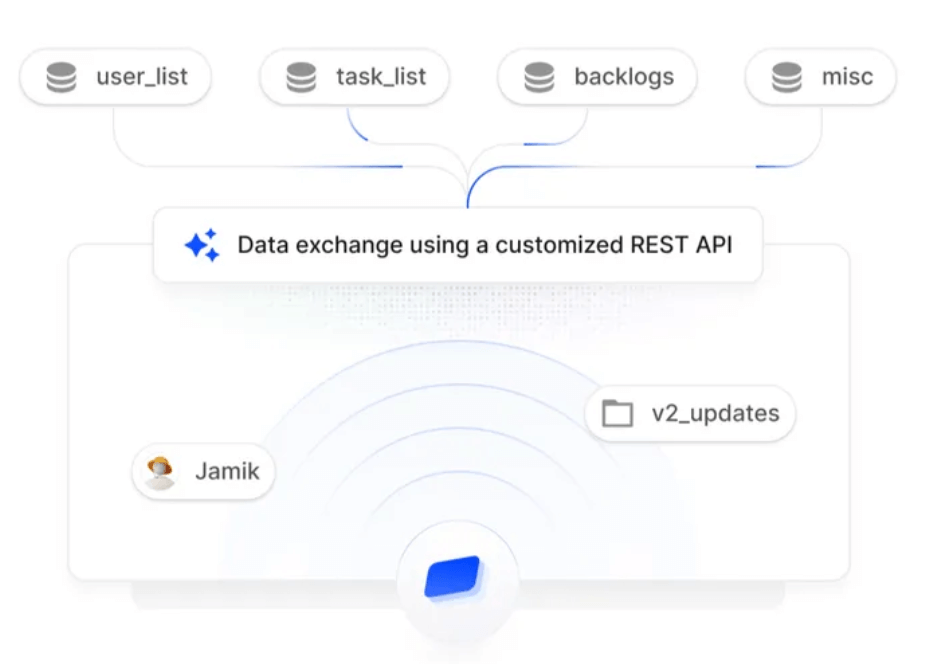
To achieve SOC 2 compliance, organizations must first assess their current practices and identify gaps in their security protocols. Following this assessment, they should implement necessary controls, conduct employee training, and engage with a certified auditor to perform the SOC 2 audit.
Start using CloudLayer and experience a new level of efficiency.